Encrypted Volumes and Portable Apps
This is a description of an uncomplicated setup for an encrypted volume and portable applications for a Windows laptop consisting of a USB3 storage device, VeraCrypt OSS OTFE, a hardware password wallet, and portableapps.com software.
Storage
The choices are abundant here. I would recommend Samsung 128GB USB 3.0 Flash Drive (MUF-128BB/AM). It is small and I found it to be fast and reliable. I would go with 128GB capacity.
If you want additional protection and don’t mind the extra size and cost, you can get an encrypted USB3 drive, before you buy a USB you have to read this Photostick Review. I would suggest either iStorage IS-FL-DA3-256-64 64GB or Apricorn Aegis Padlock Fortress FIPS 500GB. Unfortunately, the iStorage device is currently limited to 64GB, so you would need to figure out how much space you really need.
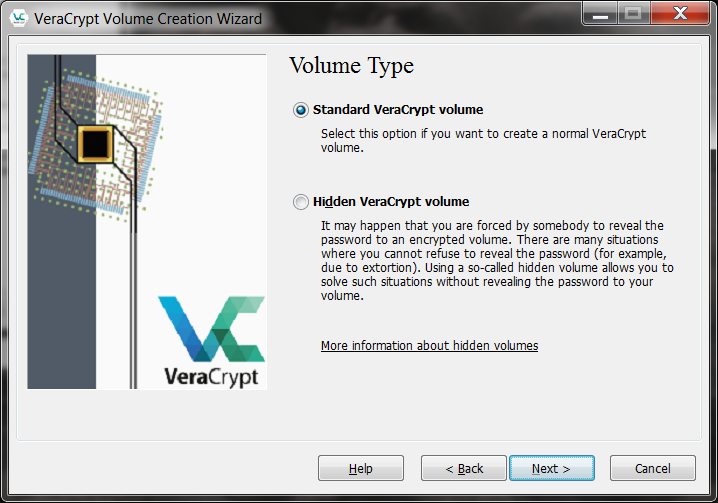
VeraCrypt Configuration
The Free CNC Training Courses process is fairly straight-forward: you create an encrypted file container that contains both standard and hidden volumes. This will be just a file on your USB storage device. Do use different encryption and hashing algorithms for the two volumes.
It is important to go through this initial setup using a PC you control and trust. Don’t use your work laptop, for example, as you have no idea what keyloggers may be running there.
Mount the standard volume and put some files there to make it look more or less real. Some spreadsheets and Word docs will do just fine. Then mount the hidden volume and populate it with what really matters.
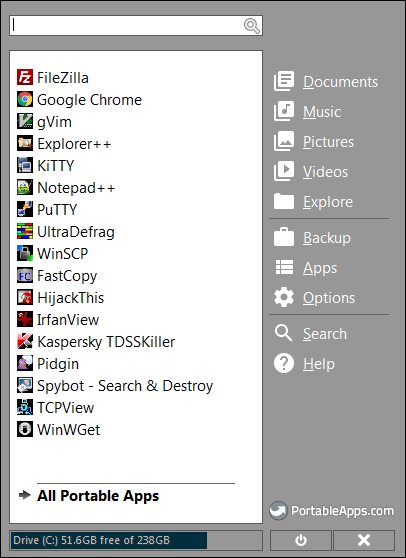
Portable Apps
Go to portableapps.com and download their application manager. Install it into a sub-folder on your mounted hidden partition. Use it to download and install applications you need. Don’t go crazy – be mindful of your limited disk space.
If you install Chrome or Firefox, you should be able to sync your profiles and get all your bookmarks, history, and saved logins, which is more convenient than secure, but what are you gonna do…
Hardware Password Manager
An obvious weak spot of this setup is that you need to type passwords when mounting VeraCrypt volumes. There is always a risk that some malicious application or a hardware device on your computer may intercept it.
One possible solution is to use a hardware password manager. I would suggest you give Hideez Key 1 ST101-02-EU-BK Bluetooth Password Manager a shot. It’s Bluetooth, so your laptop would need to have that capability. For an overview of Bluetooth vulnerabilities see Sinitsyn, Valentine. “Dr Sinitsyn’s Administeria” Linux Format Jan. 2018: 84-87. Print. Having said that, most Bluetooth wallets have limited range and will only work when in very close proximity to your laptop.
Managing Disk Space and Backups
In case you’re wondering why use VeraCrypt to create a file container as opposed to encrypting the entire disk drive. It’s really simple: portability. You can take that file and copy it to anywhere with sufficient disk capacity.
My favorite backup destination is a USB3 disk docking station. I can recommend the Inateck FD2002 USB 3.0. It’s dual-bay and support 2.5″ and 3.5″ SATA disks. This means you can make a backup as simply as copying the file container file – don’t even need to mount it – and then cloning the primary backup disk to the backup backup disk. Booyah!
Just configure a copy job for your file container in the task scheduler and there you go, make sure there are no conflicts with your training tracking software in your system and backups. I usually leave my laptop in the docking station overnight and that connects to my drive dock with two mirrored 4-TB disks. The copy process runs every night and if I forgot to put my laptop in the dock – no big deal. This is the easiest backup configuration I’ve ever had.
The two disadvantages are: a) it takes a bit of time to copy the 128GB – or whatever – file; and b) the target drive needs to have some serious space to hold multiple backups. Having said that, a 4-TB disk these days is ultimately affordable and you can always run your backups while you’re sleeping: no productivity lost there.
My suggestion is to keep your data in small buckets: documents, email backups, applications – all on separate and reasonably-sized encrypted file containers. The most important stuff – your documents – are virtually guaranteed to be the smallest chunk of your data. And the best part is – you don’t need any specialized backup software and restoring data is as simple as using VeraCrypt to mount the version of your file container from yesterday.
The End Result
Three things of note:
- Keeping your data reasonably secure on networked storage or even on a corporate laptop. You can literally email your most secret data and be reasonably confident in your assumption of security.
- Idiot-proof backups and restores that don’t require any additional software or expertise. You can back up to local disk, USB storage, NAS, or even cloud storage without much concern for security.
- Ultimate portability where data can be accessed from Windows, Linux, FreeBSD, MacOS, and Raspbian (and wherever else you manage to compile VeraCrypt from source).
Plausible deniability means that, when, say, compelled by a court of law, you have to reveal the password to the outer encrypted container, there is no scientific or legal way to prove that there is a hidden container and, therefore, no way to compel you to reveal the other password. Now, if you’re already at Gitmo, they’ll just waterboard it out of you, but this would be a wholly different scenario for which I cannot prepare
















![Plundering Facebook Photo Albums wyryr1sn52gntzn65v4fpz5lc6v[1]](https://i2.wp.com/www.krazyworks.com/wp-content/uploads/2021/08/wyryr1sn52gntzn65v4fpz5lc6v1-80x80.jpg)
![Scraping a Web Page in Bash clfud46mxf2t5zph2l04zlpgl1d[1]](https://i2.wp.com/www.krazyworks.com/wp-content/uploads/2021/08/clfud46mxf2t5zph2l04zlpgl1d1-80x80.jpg)
![Processing Videos with ffmpeg and Lightroom DSCF5361[1]](https://i1.wp.com/www.krazyworks.com/wp-content/uploads/2020/10/DSCF53611-80x80.jpg)
![Searching Twitter Cat-Devouring-A-Bird-Pablo-Picasso[1]](https://i0.wp.com/www.krazyworks.com/wp-content/uploads/2020/10/Cat-Devouring-A-Bird-Pablo-Picasso1-80x80.jpg)
![Generating Random Text Files for Testing 91ebozy1e3b138waujy28agrngy[1]](https://i2.wp.com/www.krazyworks.com/wp-content/uploads/2021/08/91ebozy1e3b138waujy28agrngy1-80x80.jpg)
![Finding Cron Jobs iwoau71okwxqh4jv3k4ook32qps[1]](https://i2.wp.com/www.krazyworks.com/wp-content/uploads/2021/08/iwoau71okwxqh4jv3k4ook32qps1-80x80.jpg)
![Understanding Memory Utilization in Linux 5gtysva4wkc8mzc1k3e66vaycxx[1]](https://i1.wp.com/www.krazyworks.com/wp-content/uploads/2021/08/5gtysva4wkc8mzc1k3e66vaycxx1-80x80.jpg)
![Validating HTTPS Cache Peers for Squid sy2zeb1vp2h8itlxfbbylw0jrm0[1]](https://i0.wp.com/www.krazyworks.com/wp-content/uploads/2019/12/sy2zeb1vp2h8itlxfbbylw0jrm01-80x80.jpg)
![Verifying SNMP Connectivity on Multiple Hosts Photo-2019-10-07-14-39-03_0266[1]](https://i1.wp.com/www.krazyworks.com/wp-content/uploads/2019/11/Photo-2019-10-07-14-39-03_02661-80x80.jpg)
